Israeli researchers show medical scans vulnerable to fake tumors
If hackers tamper with CTs or MRIs they could aid in insurance fraud, ransomware, cyberterrorism or even murder, Ben-Gurion University team says

Hackers have the ability to access the 3-D medical scans of patients and add or remove images of malignant tumors, placing patients at risk of misdiagnosis, cybersecurity researchers at Ben-Gurion University of the Negev have found.
In a new study, the researchers showed that scans they managed to alter successfully deceived both radiologists and the artificial intelligence algorithms they used to aid them with the diagnosis.
Three-dimensional computerized tomography (CT) scans combine a series of X-ray images taken from different angles around the body and use computer processing to create cross-sectional images of bones, blood vessels and soft tissues. CT scan images provide more detailed information than standard X-rays, and are used to diagnose cancer, heart disease, infectious diseases, and more. Magnetic resonance imaging (MRI) scans are similar, but use powerful magnetic fields to diagnose bone, joint, ligament, and cartilage conditions.
Deliberately tampering with these kinds of scans could facilitate insurance fraud, ransomware, cyberterrorism or even murder, the researchers said in a statement.
In a YouTube video the researchers showed how easy it is for individuals to get access to radiologist workstations at a hospital, entering from the waiting room, and install a device that is able to intercept and manipulate the data.
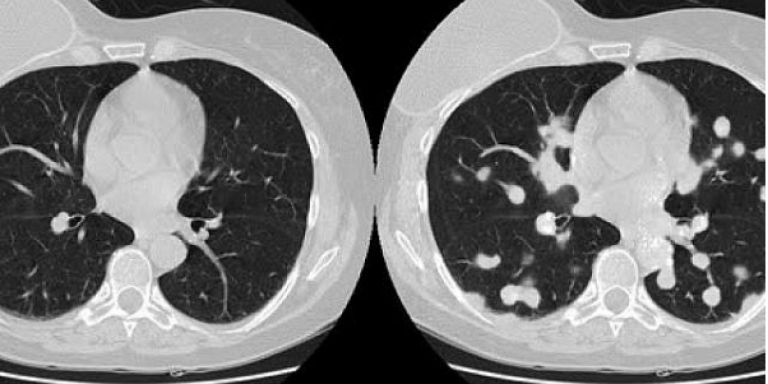
“Our research shows how an attacker can realistically add or remove medical conditions from CT and MRI scans,” said Dr. Yisroel Mirsky, lead researcher in the BGU Department of Software and Information Systems Engineering (SISE), and project manager and cybersecurity researcher at BGU’s National Cyber Security Research Center. “In particular, we show how easily an attacker can access a hospital’s network, and then inject or remove (images of) lung cancer from a patient’s CT scan.”
The attacker has the ability to take full control over the number, size and locations of tumors while preserving the anatomy from the original, full resolution 3-D image.
To demonstrate how the attack can be undertaken, the researchers asked for permission and then broke into the network of an actual hospital, managing to intercept every scan taken by a CT machine.
“The scans were not encrypted because the internal network is usually not connected to the internet. However, determined intruders can still gain access via the hospital’s Wi-Fi or physical access to the infrastructure,” Mirsky said. Moreover, “these networks are now being connected to the internet as well, which enables attackers to perform remote attacks.”
To insert and remove medical conditions, the researchers used a deep learning neural network called a generative adversarial network (GAN). GANs have been used to generate realistic imagery, such as portraits of nonexistent people. The researchers showed how these could now be used to efficiently manipulate high resolution 3-D medical imagery. The researchers used two of these GANs in their software they called CT-Gan: one trained to inject cancer and the other trained to remove cancer.
The BGU researchers verified the attack effectiveness by training their CT-GAN to inject or remove lung cancer using free medical imagery off the internet. They hired three radiologists to diagnose a mix of 70 tampered and 30 authentic CT scans.
The radiologists misdiagnosed 99 percent of the altered scans that showed malignant tumors, and 94 percent of altered images that had cancerous images removed.
After informing the radiologists of the manipulation, the experts still could not differentiate between the tampered and authentic images, misdiagnosing 60 percent of altered scans that falsely showed tumors and 87 percent of those that falsely showed no sign of tumor.
The CT-Gan was also able to fool AI-based algorithms that are meant to help radiologists in their diagnosis, Mirsky said. “Consequently, the state-of-the-art artificial intelligence lung cancer screening tools, used by some radiologists, are also vulnerable to this attack.”
What can be done?
In their paper, the researchers propose some immediate countermeasures to mitigate most of the threat.
One solution is to enable encryption between the hosts in the hospital’s radiology network. In addition, some hospitals should install digital signatures so that their scanners sign each scan with a secure mark of authenticity.
“Another method for testing the integrity of the images is to perform digital watermarking (DW), the process of adding a hidden signal into the image such that tampering corrupts the signal and thus indicates a loss of integrity,” Mirsky said. “Unfortunately, the vast majority of medical devices and products currently do not implement DW techniques.”
Other researchers who participated in the study were Prof. Yuval Elovici, PhD, director of the Telekom Innovation Labs@BGU and director of Cyber@BGU; Tom Mahler, PhD candidate and researcher at Cyber@BGU and a member of the BGU SISE; and Prof. Ilan Shelef, MD, PhD, director of the imaging department in Soroka University Medical Center and a member of the BGU Faculty of Health Sciences.